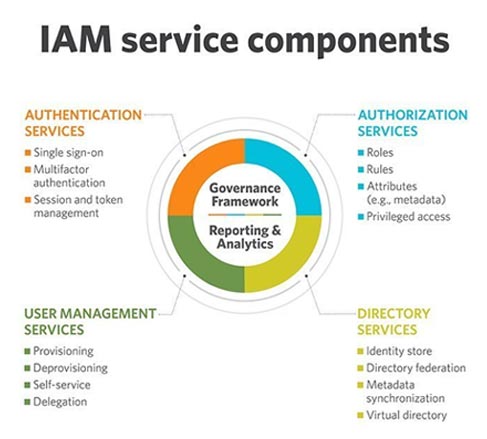
Identity and Access Management lets the right individuals access the right enterprise resources (applications, databases, networks, etc.) at the right time for the right reasons.
With an IAM framework in place, IT managers can control user access to critical information within their organizations. Systems used for IAM include single sign-on systems, two-factor authentication, multifactor authentication and privileged access management. These technologies also provide the ability to securely store identity and profile data as well as data governance functions to ensure that only data that is necessary and relevant is shared.
Businesses leaders and IT departments are under increased regulatory and organizational pressure to protect access to corporate resources. As a result, they can no longer rely on manual and error-prone processes to assign and track user privileges. IAM automates these tasks and enables granular access control and auditing of all corporate assets on premises and in the cloud.
IAM, which has an ever-increasing list of features — including biometrics, behavior analytics and AI — is well suited to the rigors of the new security landscape. For example, IAM’s tight control of resource access in highly distributed and dynamic environments aligns with the industry’s transition from firewalls to zero-trust models and with the security requirements of IoT. For more information on the future of IoT security, check out this video.
Manage user identities: IAM systems can be the sole directory used to create, modify, and delete users, or it may integrate with one or more other directories and synchronize with them. Identity and access management can also create new identities for users who need a specialized type of access to an organization’s tools.
Provisioning and deprovisioning users: Specifying which tools and access levels (editor, viewer, administrator) to grant a user is called provisioning. IAM tools allow IT departments to provision users by role, department, or other grouping in consultation with the managers of that department. Since it is time consuming to specify each individual’s access to every resource, identity management systems enable provisioning via policies defined based on role-based access control (RBAC). Users are assigned one or more roles, usually based on job function, and the RBAC IAM system automatically grants them access. Provisioning also works in reverse; to avoid security risks presented by ex-employees retaining access to systems, IAM allows your organization to quickly remove their access.
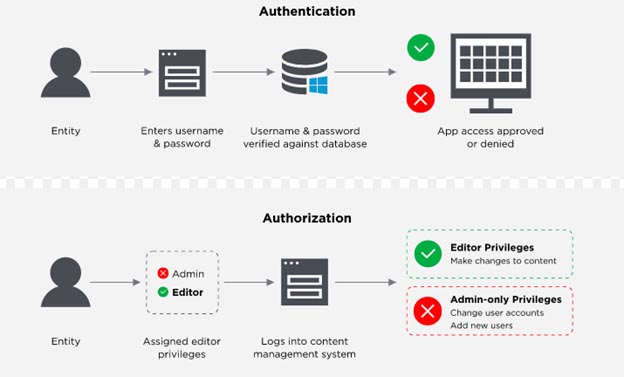
Authenticating users: IAM systems authenticate a user by confirming that they are who they say they are. Today, secure authentication means multi-factor authentication (MFA) and, preferably, adaptive authentication.
Authorizing users: Access management ensures a user is granted the exact level and type of access to a tool that they’re entitled to. Users can also be portioned into groups or roles so large cohorts of users can be granted the same privileges.
Adaptive Multi-Factor Authentication: Most IAM solutions provide Adaptive Multi-Factor Authentication (MFA) functionality to protect against impersonation and credential theft. With MFA, a user must present multiple forms of evidence to gain access to a system, for example, a password or fingerprint and an SMS code. Modern MFA solutions support adaptive authentication methods, using contextual information (location, time-of-day, IP address, device type, etc.) and administratively defined policies to determine which authentication factors to apply to a particular user in a specific situation.
Single Sign-On: Identity and access management solutions with single sign-on (SSO) allow users to authenticate their identity with one portal instead of many different resources. Once authenticated, the IAM system acts as the source of identity truth for the other resources available to the user, removing the requirement for the user to remember several passwords.
Reporting: IAM tools generate reports after most actions taken on the platform (like login time, systems accessed, and type of authentication) to ensure compliance and assess security risks.
IAM technologies can be used to initiate, capture, record and manage user identities and their related access permissions in an automated manner. An organization gains the following IAM benefits:
Companies can gain competitive advantages by implementing IAM tools and following related best practices. For example, IAM technologies allow the business to give users outside the organization — like customers, partners, contractors, and suppliers — access to its network across mobile applications, on-premises applications and SaaS without compromising security. This enables better collaboration, enhanced productivity, increased efficiency and reduced operating costs.
© Ascent InfoSec 2024 | All Rights Reserved