Security, Identity, and Compliance on AWS
Security is one of the critical concerns for all companies considering or already leveraging cloud. It could be an enterprise, a small/medium-sized business, or a startup company, and we all worry about the safety and security of our data.
Security at AWS is job zero for every tenant, and it begins with taking a more proactive approach to infrastructure security. It’s even more important than any number one priority of AWS. It doesn’t rely on the specific protective or reactive third-party security tools, but instead builds security into your infrastructure from the ground up.
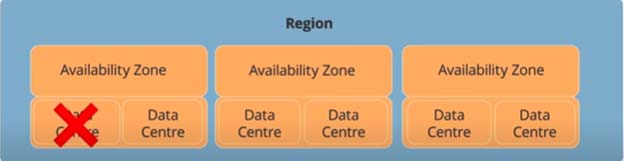
Security in AWS is everybody’s responsibility, and it starts right from the infrastructure (Regions, Availability zones, and Data centers.)
Availability zones are the physical data centers, and they are designed to be fault-tolerant and highly available. Availability zones are always in a group of two or more, and if one data center goes down for any reason, there will still have the services running from the second data center.
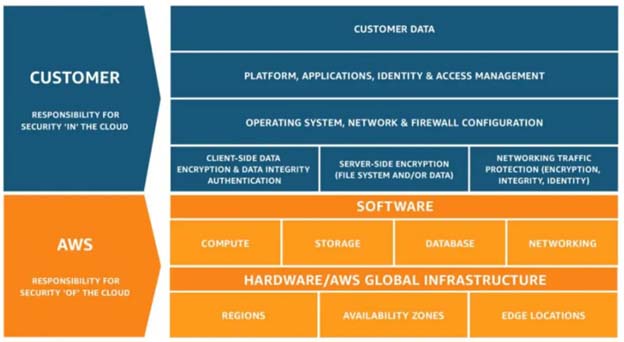
AWS has a shared security responsibility model, where AWS say that whatever happens to the underlying infrastructure (hardware, software, networking, and facilities that run AWS services). They are responsible for securing that infrastructure, such as the regions, the availability zones, and the edge location. They are responsible for that underlying infrastructure.
The customers are responsible for everything that they put on top of that infrastructure (Amazon EC2, storage, databases, Amazon VPC, and more), including the data, the applications, the access, the firewall rules, etc. The tenant is responsible for configuring access to anybody on that infrastructure.
AWS Shared security responsibility model
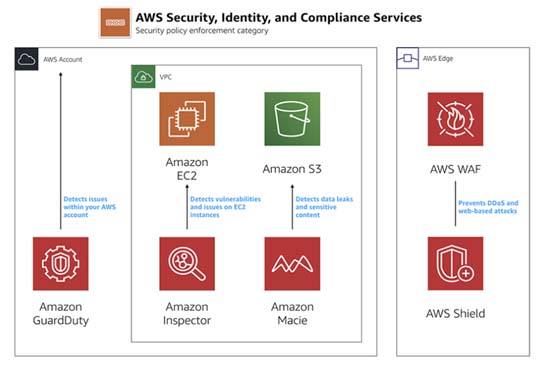
By default, AWS provides all the tools, and they do not give any access to firewalls, any user that we create, or any object that we upload to the cloud. By default, it will be private, and need to explicity make that as public as needed. We must explicitly give permissions for the user to the functionality.
Whenever we add any data, then it is addressed. We have to assign who can access it. AWS gives you a whole set of services to secure your data, applications, and resources such as servers in the cloud.
AWS Identity and Access Management
AWS starts from the identity and access management. To discover, determine, and understand the essential, core, or most important aspects of some issue, the problem of accessing your system, and then what they are allowed to do in that system. They are called authentication and authorization.
AWS gives you so many options to create users, create rules, manage the credentials on your own, or have something called Identity Federation, so you don’t have to create a login for everyone. If you already have their credentials in your Active Directory, or if you want to connect with Facebook ID or Gmail ID or LinkedIn ID, or Twitter ID. AWS should be able to do that, and this is known as identity federation, and it allows you to do just that.
AWS also has something called roles where AWS manages the credentials. They are rotated internally, so you don’t have to worry about managing credentials, or storing them in the servers, or passing them to the API request.
AWS STS: AWS Security Token Service is a web service that enables you to request temporary, limited-privilege credentials for AWS Identity and Access Management (IAM) users or for users that you authenticate (federated users). You can allow somebody to access your application or system for a few minutes, or maybe 60 minutes, or maybe up to a few hours, and then these tokens would automatically expire.
AWS Multi-Factor Authentication (MFA): It is a simple best practice that adds an extra layer of protection on top of your username and password and will help protect your AWS resources. You can enable MFA for IAM users or the AWS account root user. When you enable MFA for the root user, it affects only the root user credentials. IAM users in the account are distinct identities with their own credentials, and each identity has its own MFA configuration. You can have all your users use this hardware or software device to authenticate themselves.
AWS WAF: AWS Web application firewall will protect all your applications. You can configure it to the best of your choices, and it will protect you from any unwanted traffic that you don’t want to hit your application.
AWS Shield: It is the service to mitigate all DDoS attacks. It comes in two versions, a standard version, and an advanced version. The standard version is free of cost. So, it will block most known DDoS and other attacks. You can configure it to protect your hardware or resources from any known attacks.
Amazon Inspector will monitor all your cloud resources continuously against any security threat. We must install an agent, and it will keep running and producing reports for you every month. Accordingly, the bill is per agent per month, and it is very economical when you compare it with other services, which are either paid or open-source and not managed.
AWS Certificate Manager is a service that manages your SSL and TLS certificate. You can bring your own certificate and upload it, or you can buy that certificate from AWS, and it both ways. You can manage those certificates in one location AWS gives you that capacity. So you don’t have this hassle of managing those services.
Security Design Principles at AWS:
Security pillar centers on protecting information, systems, and assets along with delivering business needs.
- Implement a strong identity foundation: Implement the least privilege and enforce authorized access to AWS resources. Design central privilege management and reduce the risk of long-term credentials.
- Enable Traceability and Security Events: Monitor, alert, and audit incident response of actions and changes in environment real-time. Run incident response simulations and use automation tools upsurge speed for detection, investigation, and recovery.
- Apply Security at All Layers: Apply security to all layers, like the network, database, OS, EC2, and applications. Prevent application and infrastructure by human and machine attacks.
- Automate Security Best Practices: Create secure architectures, including implementation of controls that are defined, software-based security mechanisms and managed as code in version-controlled templates.
- Safeguard Data in Transit and At Rest: Categorize data into sensitivity levels and mechanisms, such as encryption, tokenization, and access control.
- Keep People Away from Data: Create mechanisms and tools to reduce or eliminate the need to direct access or manual processing of data to reduce the risk of loss due to human error.
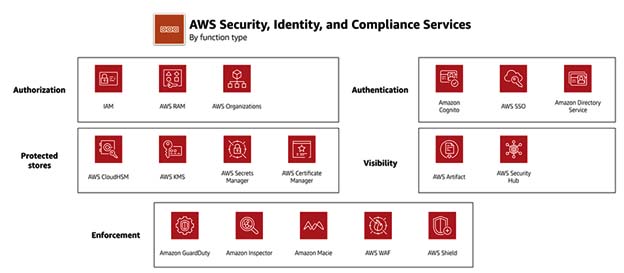
AWS Security, Identity, & Compliance services
Please find below Category, Use cases and AWS services.
1. Identity & access management
- Securely manage access to services and resources – AWS Identity & Access Management (IAM)
- Cloud single-sign-on (SSO) service – AWS Single Sign-On
- Identity management for your apps – Amazon Cognito
- Managed Microsoft Active Directory – AWS Directory Service
- Simple, secure service to share AWS resources – AWS Resource Access Manager
- Central governance and management across AWS accounts – AWS Organizations
2. Detection (Logging and monitoring)
- Unified security and compliance center – AWS Security Hub
- Managed threat detection service – Amazon GuardDuty
- Analyze application security – Amazon Inspector
- Record and evaluate configurations of your AWS resources – AWS Config
- Track user activity and API usage – AWS CloudTrail
- Security management for IoT devices – AWS IoT Device Defender
3. Infrastructure Protection
- Network security – AWS Network Firewall
- DDoS protection – AWS Shield
- Filter malicious web traffic – AWS Web Application Firewall (WAF)
- Central management of firewall rules – AWS Firewall Manager
4. Data protection
- Discover and protect your sensitive data at scale – Amazon Macie
- Key storage and management – AWS Key Management Service (KMS)
- Hardware based key storage for regulatory compliance – AWS CloudHSM
- Provision, manage, and deploy public and private SSL/TLS certificates – AWS Certificate Manager
- Rotate, manage, and retrieve secrets – AWS Secrets Manager
5. Incident response
- Investigate potential security issues – Amazon Detective
- Fast, automated, cost- effective disaster recovery – CloudEndure Disaster Recovery(KMS)
6. Compliance
- No cost, self-service portal for on-demand access to AWS’ compliance reports – AWS Artifact
- Continuously audit your AWS usage to simplify how you assess risk and compliance – AWS Audit Manager
Good reads:
https://aws.amazon.com/products/security/
https://dzone.com/articles/pillars-of-aws-well-architected-framework
https://docs.aws.amazon.com/whitepapers/latest/aws-overview-security-processes/welcome.html
Ascent InfoSec, the cybersecurity focus of Ascent Innovations LLC
- Microsoft Partner for providing Cloud Solutions in Chicago, Illinois
- Top Managed Security Service Providers (MSSPs) in Chicago, Illinois
- Inc 5000 Fastest Growing Companies in US
- Best Managed Security Services Providers in Chicago, Illinois

