What is a Web Application Firewall (WAF)?
A Web Application Firewall (WAF) helps protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet traffic and by blocking bad HTTP traffic, malicious web service requests, and automated botnets attack. By inspecting the traffic, it can prevent attacks exploiting a web application’s known vulnerabilities, such as SQL injection, cross-Site Request Forgery (CSRF), cross-site scripting (XSS), DDoS attacks, cookie poisoning, file inclusion, improper system configuration, and more.
While proxies generally protect clients, WAFs protect servers from most common attacks faced by web applications. A WAF is deployed to protect a specific web application or set of web applications. A WAF can be considered a reverse proxy protecting the servers from exposure by having clients pass through the WAF before reaching the server.
WAFs are especially useful to companies that provide products or services over the Internet, such as e-commerce shopping, online banking, and other interactions between customers or business partners. With the growth in Software as a Service (SaaS), web application security is growingly becoming a critical security element for any online interaction.
How does a web application firewall (WAF) work?
WAFs are deployed as host-based (software), network-based (hardware appliance), or cloud-based, and operate with a specific set of rules called policies. These policies tell the WAF what vulnerabilities, loopholes, or traffic behavior to look for, what to do in the event of vulnerabilities being detected, etc. In other words, the policies are what enable WAF to secure the web applications and servers from attacks.
Based on these policies, A WAF analyzes Hypertext Transfer Protocol (HTTP) requests and applies a set of rules that define what parts of that conversation are good and what parts are malicious. The main parts of HTTP conversations that a WAF analyzes are GET and POST requests. GET requests are used to retrieve data from the server, and POST requests are used to send data to a server to change its state.
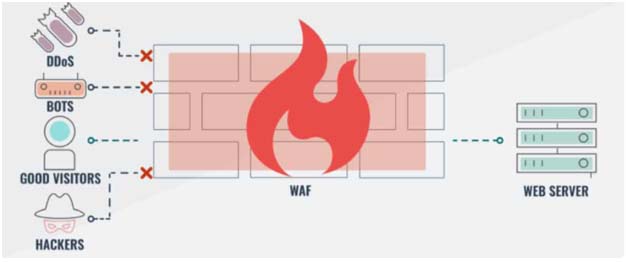
A Web Application Firewall is generally configured according to three basic security approach:
Whitelisting approach: It allows only pre-approved traffic that meets specifically configured criteria. It will deny all requests by default and allow only requests that are known to be trusted. This approach is best suited for use on internal networks that are used only by a limited group of users (for instance, employees). This is because whitelisting can block legitimate requests and traffic too, when used on public websites and applications.
Blacklisting approach: It blocks known vulnerabilities, attack signatures, malicious actors, malicious web traffic, and protect vulnerabilities of web servers or web applications. For example, if some external IP addresses are sending more requests than is typical, the blacklisting WAF can secure the application against a DDoS attack. This security approach is best suited for web applications on the public internet as legitimate requests can come from unfamiliar client machines. However, this approach is not effective against zero-day attacks.
Hybrid Security model: A hybrid security model uses elements of both blacklisting and whitelisting methods based on the specific needs of the application. It can be used on both internal and external networks.
For many organizations, WAFs are a trusted, first line of defense for applications, primarily to protect against the Open Web Application Security Project (OWASP) Top 10 risks — the foundational list of the most seen application vulnerabilities. WAFs have standards rules embedded in it, but your server administrator can adjust these and add on custom rules as well.
Top 10 Web Application Security Risks are:
- Injection attacks
- Broken Authentication
- Sensitive data exposure
- XML External Entities (XXE)
- Broken Access control
- Security misconfigurations
- Cross Site Scripting (XSS)
- Insecure Deserialization
- Using Components with Known Vulnerabilities
- Insufficient Logging & Monitoring
What Attacks do WAFs protect against?
A web application firewall needs to protect your web server and its content from the following categories of attacks:
- Cross-Site Scripting (XSS) – malicious HTML code inserted into a web page input field by a hacker.
- Structured Query Language (SQL) injection – SQL attacks can affect any application that uses an SQL database and enables attackers to access and potentially change sensitive data.
- Web session hacking – It enables attackers to hijack a session ID and masquerade as an authorized user. A session ID is normally stored within a cookie or Uniform Resource Locator (URL).
- Hidden field manipulation – hackers rewrite the source code of a web page to alter values held in hidden fields and then post the amended code back to the server.
- Cookie poisoning – altering parameter values held in cookies to corrupt data passed between web pages
- Web scraping – automated data extraction from web pages.
- Layer 7 DoS attacks – overwhelming a web server by recursive application activity.
- Parameter tampering – altering values in the parameters to a web page call.
- Buffer overflow – user input that overwrites the code in memory.
- Backdoor or Debug options – developer feedback reports for web page testing that can be used by hackers for access to the processor.
- Stealth commanding – an attack on the operating system of a web server.
- Forced browsing – the hacker gains access to backup or temporary folders on the web server.
- Third-party misconfigurations – manipulation of content inserts provided by other companies.
- Site vulnerabilities / SQL injections – queries entered in user authentication fields.
Available Solutions
Most commercial WAFs have similar features, but major differences often refer to user interfaces, deployment options, or requirements within specific environments. Some of the widely used products are Signal Sciences, Cloudflare, Sucuri, F5, Wallarm, Radware, AWS, Microsoft, Fortinet, Citrix, Radware, and many more (not in any order).
The newer WAF tools come with integration with threat intelligence feeds, intrusion prevention and a built-in load-balancer. Integrated threat feeds enable the WAF tools to respond to threats in real-time and has the potential for machine learning and in some cases apply rules automatically. The major downside with automatic updates is that the updates are applied without testing and can even make the application unavailable.
Every software available over the web, whether hosted in your own data center or in a major cloud platform like Azure or AWS, must be evaluated for the potential attacks and exploitation of vulnerabilities.
Ascent InfoSec, the cybersecurity focus of Ascent Innovations LLC
- Microsoft Partner for providing Cloud Solutions in Chicago, Illinois
- Top Managed Security Service Providers (MSSPs) in Chicago, Illinois
- Inc 5000 Fastest Growing Companies in US
- Best Managed Security Services Providers in Chicago, Illinois

